Parameter tampering cyberattack and event-trigger detection in game-based interactive demand response - ScienceDirect

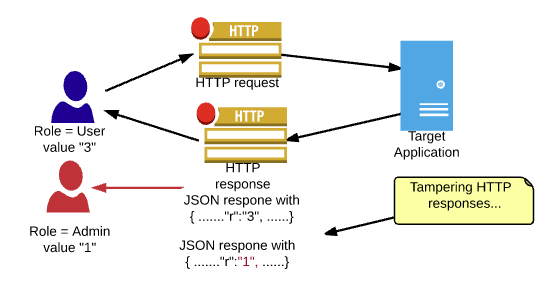
An example of a configuration data tampering attack 3.3. Variable data... | Download Scientific Diagram

The Risks of Data Tampering and How to Prevent It - Ocala, Gainesville, Orlando | Verteks Consulting, Inc.

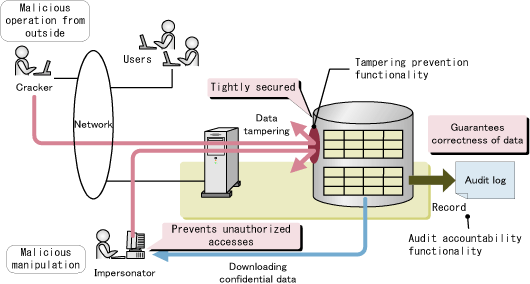
Database Tampering and Detection of Data Fraud by Using the Forensic Scrutiny Technique | Semantic Scholar